An Ultimate Guide to Deepfakes 2024
Author: teresa_myers | 16 May 2024In This Post
Is Deepfake AI technology moving in the direction it was intended to?
There’s a lot of discussion and ongoing debate on deepfake technology since access to Artificial Intelligence tools has become easy. Deepfake creation was initially used for entertainment, where multiple apps offered a funnier way to create a deepfake. As the technical advancement in AI hit the road, cyberattackers, and fraudsters started using deepfake to bypass identity management and security systems on multiple online platforms. Most of these deepfake attacks were aimed at financial gains, manipulation, and defamation of celebrities and other individuals. Here, we cannot ignore the use of deepfake pornography for extortion, threatening, and sexual gains as it is highly damaging to the very digital existence of people.
In this article, we will provide a handy knowledge builder to help you develop your understanding of Deepfake Technology and how its negative use can be deterred to protect digital identities. We will also provide some proven preventive measures against deepfake threats in online activities.
Key Takeaways
- Deepfakes are mostly created through AI which are highly realistic and convincing facial images used to spoof facial recognition systems.
- Multiple sophisticated technologies are employed to create a deepfake image or a video including facial morphing.
- Deepfakes initially had positive uses but not their dominant use is for illicit purposes.
- Celebrity deepfake is a rising concern posing a serious threat to the integrity and goodwill of famous personnel around the world.
- A Deepfake attack is carried out in both 2D and 3D images and videos.
- Deepfake detection technology mainly relies on facial recognition solutions having both active and passive liveness detection mechanisms.
- Third-party facial recognition solutions can play a vital role in streamlining the prevention and detection of deepfakes.
What is Deepfake?
Originally, deepfake referred to synthetic media that is manipulated digitally to replace a human identity with another convincingly. A deepfake can both exist or be nonexistent in real life for example:
- A deepfake of a real-life person say a celebrity like the famous Hollywood actor Jake Gyllenhaal deepfake used by a person.
- A fully new deepfake created by graphic tools to be used as a new identity. Mostly, it is used to spoof identity verification tools.
The word ‘deepfake’ is derived from ‘deep learning’ and ‘fake’.
What is Deepfake Technology?
Deepfake technology is the sophisticated means of creating deepfakes by employing the latest online software and apps available. Mostly deepfakes are created online through available tools and require graphic designing skills. The more advanced a deepfake technology and graphic skills are, the higher the deepfake image or video quality in realistic and convincing.
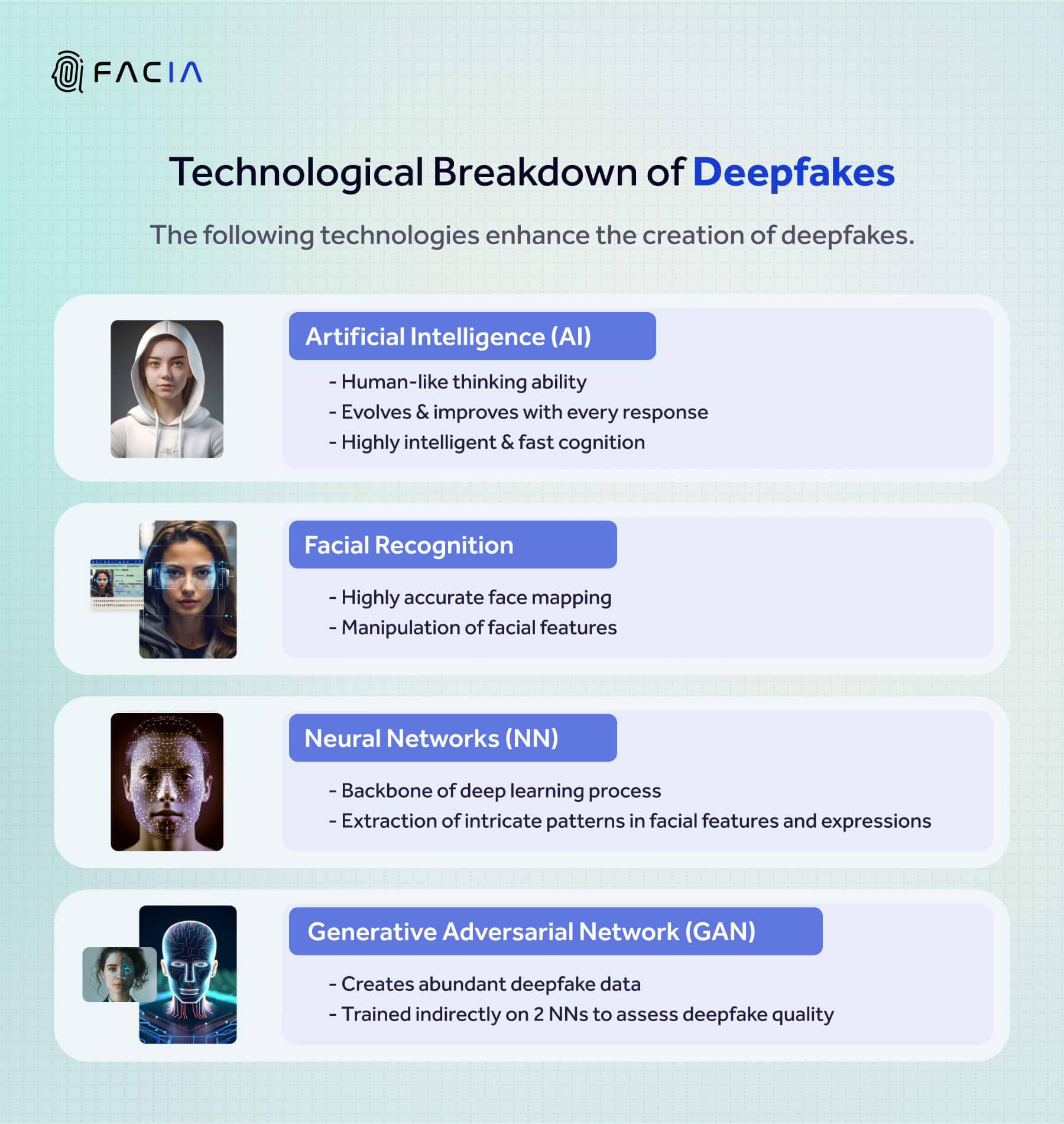
How are Deepfakes created?
The following technologies are leveraged while creating a deepfake.
| Artificial Intelligence |
|
| Facial Recognition Algorithms |
|
| Neural Networks |
|
| Generative Adversarial Network (GAN) Model |
|
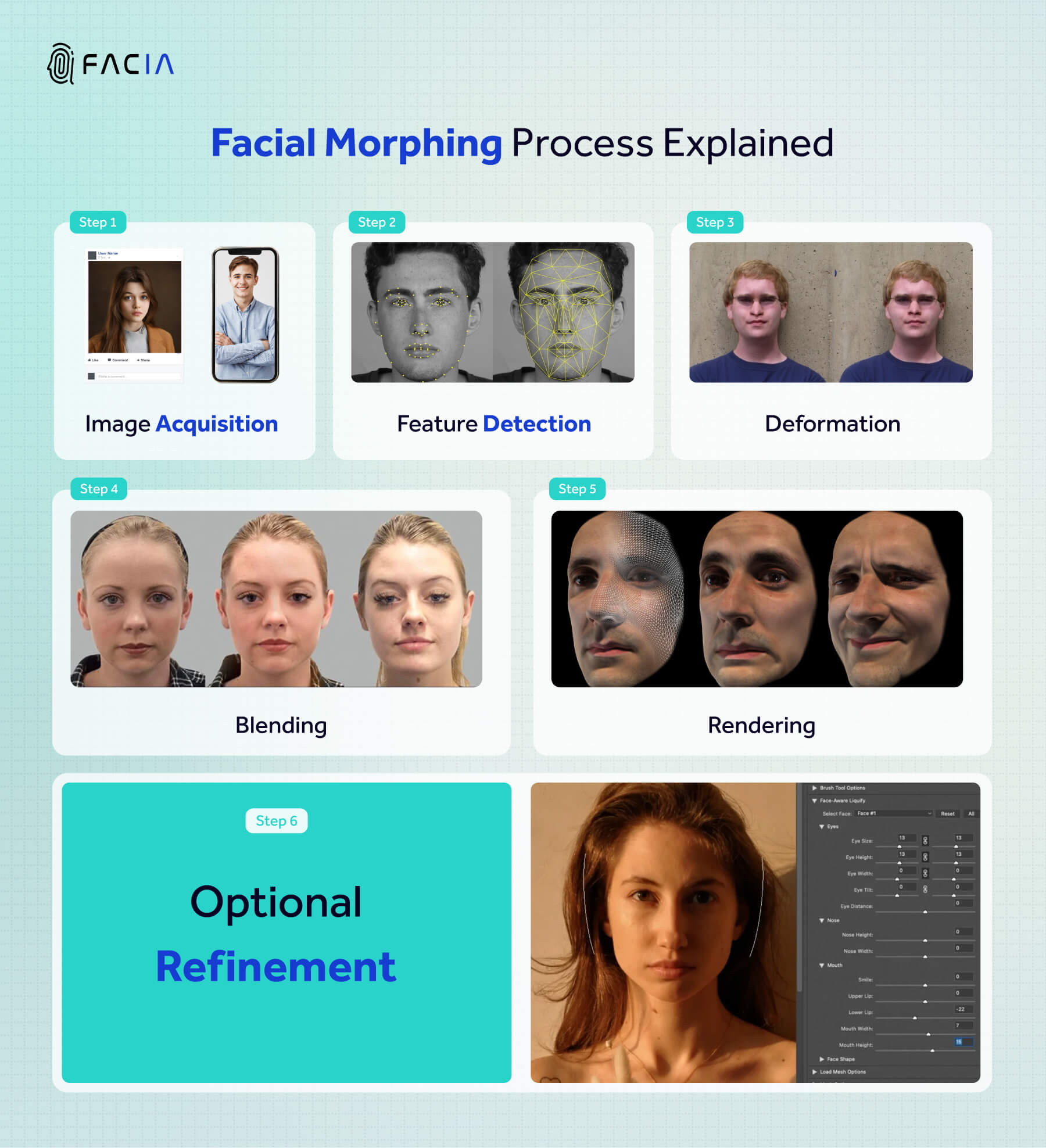
Facial Morphing Supplementing Deepfakes
Facial Morphing is another technique that supplements the creation of deepfakes and facilitates AI Face Swapping through image blending techniques. Facial morphing is one of the key tactics used for deepfake verification.
Here’s how it works:
How are Deepfakes Used?
Deepfakes were initially created by online community users for entertainment purposes in the early 1990s. Image manipulation also existed in the 19th century, but considering digital image and video manipulation, deepfakes are relatively new. Especially the use of Generative AI has enabled the creation of highly realistic deepfake photos, videos, voice clones, and even digital replicas.
Deepfakes have both positive and negative uses.
Positive Uses
- Deepfakes are used on social media platforms for creating memes and other entertainment-purpose content. It supplements the creation of amusing content like parodies, satire, etc.
- Deepfakes are used for recreational content such as historical events making learning sessions more interactive.
- Deepfakes have helped the film industry in multiple ways, for example, by de-aging legendary actors, allowing CGI effects and even resurrecting dead actors for guest appearances. The film production houses are bound to pay royalties to actors whose deepfakes are created.
- Advertisement and Marketing have become highly influential where deepfakes have improved the celebrity endorsement part and other aspects of branding in visual content marketing.
Negative Uses
- Identity Fraud is the most pressing issue that uses deepfake images, deepfake videos, etc to bypass identity verification. Mostly facial recognition and voice recognition systems are spoofed using AI deepfakes of facial images and voice cloning techniques.
- Misinformation and fake news are spread using deepfakes of people.
- Reputational damage is caused by deepfake pornography and other deepfakes which can be due to revenge or monetary gains.
- Serious security concerns are raised due to deepfake usage for bypassing credentials required to enter sensitive premises.
- Deepfake scams also result in crimes like catfishing, phishing, credit card fraud, etc.
- Deepfakes in politics can negatively influence political campaigns, cause public unrest, and create mass confusion.
Celebrity Deepfakes – A Rising Issue
Celebrity Deepfakes are intended to be used positively. However, this graphical creation has caused serious reputational damage and stress to many celebrities as perpetrators have used celebrity deepfakes for revenge pornography, defamation, or spreading false news about the targeted celebrity.
Here are some celebrity deepfakes that recently hit the internet:
- Katty Perry’s Deepfake at the recent Met Gala 2024 dressed her in the theme that she reportedly didn’t even attend the gala.
- Tom Hanks’s deepfake was created to promote a fake dental plan last year.
- Vladimir Putin (Russia’s president) was a target of a deepfake video of his.
Other famous personalities who have been targets of deepfake include ex-President Barak Obama, Famous singer Taylor Swift, Actor Tom Cruise, and many others.
Is Making Deepfake a Crime?
Not exactly!
Creating deepfakes itself is not a crime. It is an AI-powered technology that can be used with both positive and negative intentions respectively. It is the criminal use of deepfakes that is questioned and now governments like the UK are stressing on making deepfake porn creation a crime. Similarly, the crimes associated with or supplemented by the use of deepfakes like crypto-fraud, crowdfunding fraud, and money laundering are serious criminal and punishable offenses.
Read the recent news: Deepfake Porn Deemed as a Crime | New Law Passes in the UK
It is a pressing concern that the use of Deepfakes must be regulated and restricted to legitimate activities only. Regulatory bodies like FCA, FinCEN, FATF, and others can contribute to regulating industries using deepfakes and protecting the digital identities of genuine users.
Types of Deepfakes
Mainly there are 4 types of deepfakes:
| It is an image manipulation technique in which a person’s entire face is morphed into the face of another facial image to create a realistic deepfake digital face. |
| Highly realistic voice clones can be made through audio deepfake tools that can be used to spoof voice recognition. |
| Complete body doubles in digital format can now be made through AI deepfake technology. They are also known as doppelgangers by combining AI face swaps, voice cloning, and body swapping. |
| Generative AI tools have enabled the creation of deepfake images and videos through prompting including text-based commands. |
The highest risk posed by the above deepfake types is through Face Swaps. These are now actually called deepfake images or deepfake videos. Most online impersonation attacks, Account takeover attempts, and identity theft cases rely on creating deepfakes. AI Face swaps have enabled a high-level of fraud and deepfake scams causing losses in huge amounts, compromising public online security and data integrity.
How a Deepfake Attack is Carried Out?
A deepfake attack is intended to spoof identity verification systems mostly in the case of facial recognition. Most deepfake attack requires two things to be successful:
- A facial recognition system has a weak Deepfake detection algorithm that is not fully capable of detecting the prevalent deepfake attack vectors.
- The time window in which a deepfake can bypass facial identity verification. Usually, it requires a few seconds.
Here’s how Deepfake attacks target the victims based on 2D or 3D-based deepfakes.
| Source | Target |
| 2D Image |
|
| 2D Video |
|
| 3D Image |
|
| 3D Video |
|
Moreover, the technical aspects of deepfake targets are mentioned in the below table. Do note that both 2D and 3D images and videos refer to the deepfake images and videos and the aspects include the data source, the level of reality, the control over deepfake in that category, and how easily it can be manipulated.
| Aspect | 2D Image | 2D Video | 3D Image | 3D Video |
| Source Data | Single frame | Video frames | Single frame | Video frames |
| Realism | Limited | Moderate | High | High |
| Control | Limited | Moderate | Moderate | High |
| Manipulation | Easy | Moderate | Moderate | Complex |
How is an AI Deepfake Face Detected?
Facial Recognition is one of the most discussed topics when it comes to detecting AI-generated deepfake facial images. Facial recognition technology is used to detect anomalies and suspicious sign-in attempts during identity verification. It requires users to submit their face images, or a video through their selfie camera. This is the area where deepfake attacks target the most through a technique called presentation attack in a 2D setting or ‘deepfake injection attack’ in both 2D and 3D facial identification systems. Pertinent to deepfake faces, Deepfake detection technology mostly relies on an AI-powered facial recognition solution that has a core feature of liveness detection.
The Critical Role of Liveness Detection in Deepfake Detection
To technically detect Deepfake faces, facial recognition relies on ‘Liveness Detection’. It is a process that is carried out by sophisticated face identity solutions to confirm that a living person has attempted verification and that the face presented to the system is not a deepfake. Liveness can be verified in two dimensions:
- Active Liveness – This is verified by prompting a user to perform certain actions and gestural movements, for example, tilting head motion, blinking, and smiling.
- Passive Liveness – It is automatically checked by the use of AI-powered liveness detection algorithms once a face is presented to the camera.
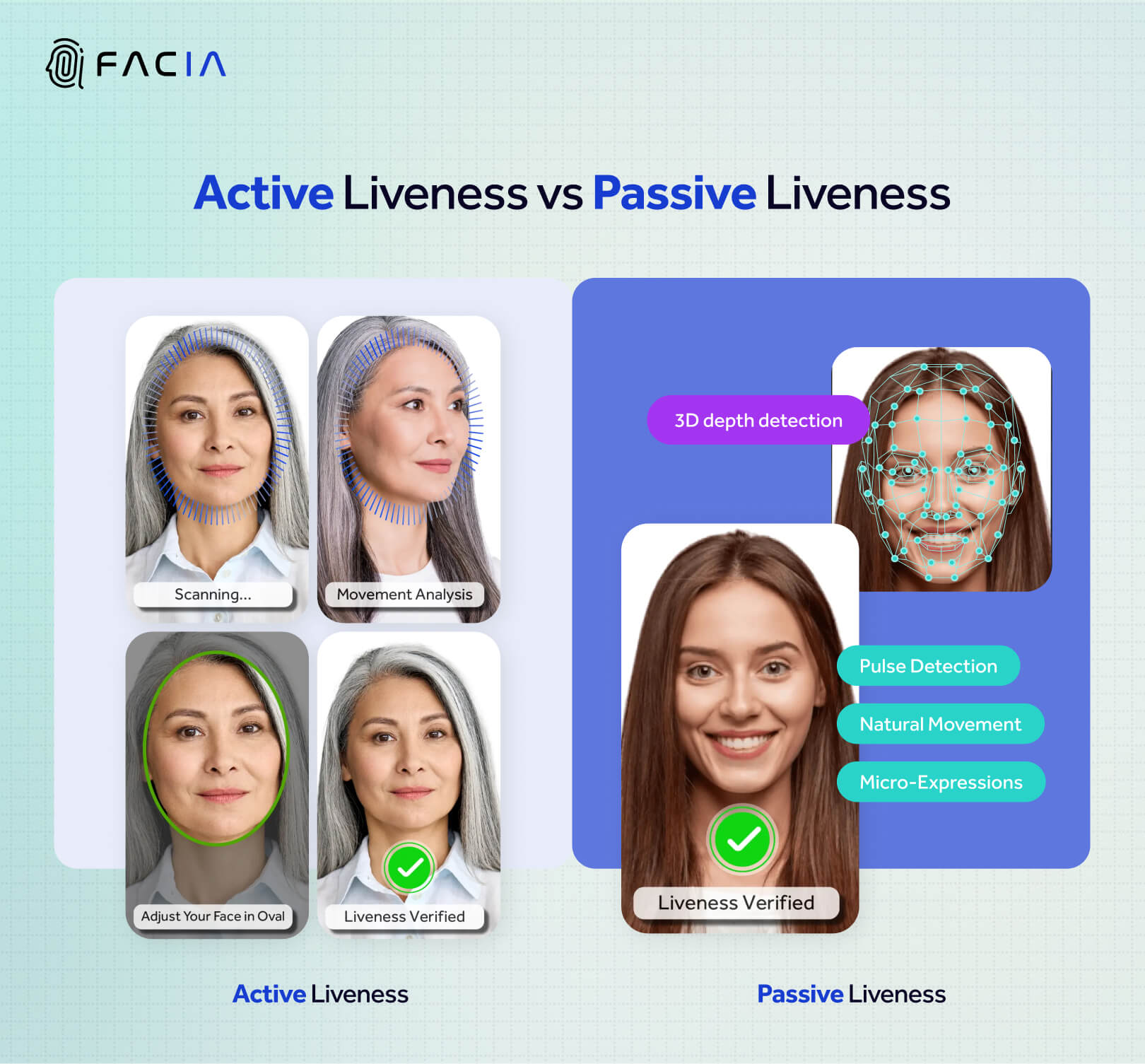
Factors of Liveness Detection
1. Speed
It is important to note that a deepfake attack requires only a few seconds to bypass facial identification. Therefore, facial recognition solutions should consider expediting their liveness checking by increasing the liveness detection speed. This requires employing high-res and high-tech cameras that can quickly capture facial images correctly and the facial recognition system should perform an accurate liveness check in both active and passive dimensions.
2. Accuracy
Also, accuracy matters in verifying the liveness of facial identity. There is a standardized approach set by the National Institute of Standards and Technology (NIST). NIST governs the benchmarking for biometric identity solutions including facial recognition technology. According to Face Technology Evaluations – FRTE/FATE, a facial biometric identity tool must:
Have the lowest number in False Non-Match Rate (FNMR) and False Match Rate (FMR) where genuine user images must not be falsely flagged as a deepfake. Ideally, it should be 0% for both.
The Need for Third-Party Facial Recognition Vendors
Recently, the UK’s Solicitor’s Regulatory Authority (SRA) updated its sectoral risk assessment on financial crimes in which it warned the solicitors against deepfake attacks in video calls with their clients. Third-party identity solutions are capable of addressing this concern.
Read the complete editorial: Analyzing Solicitors Regulation Authority (SRA)’s Update | Highlighting Deepfake Threat to Law Practitioners
Despite this, third-party identity solutions can benefit firms and businesses in multiple ways against deepfake threats.
- Efficient budget allocation of Regulatory compliance through digital identity management
- Overall time reduction in KYC (Know Your Customer) through smart identity verification
- Increasing customer trust in businesses by protecting their online digital presence.
- Offering an array of identity solutions under one umbrella
- Reducing the firm’s investment of time and resources in identity verification
Stay Ahead of Deepfake Threats with Facia
Facia is an AI-powered facial identification tool that swiftly recognizes suspicions in a facial image or a video of any sort. Covering a wide range of facial identity threat detection mechanisms, Facia empowers users to authenticate their digital identities safely and enables businesses to validate their customers without facing deepfake attacks. Facia ensures the complete Liveness Verification in under 1 second alongside a 0% False Acceptance Rate ensuring that no deepfake goes undetected.
With Facia’s uniquely programmed Deepfake Detector ‘Morpheus AI’, we recognize the need to detect deepfake images and videos created by more than 100,000 software in the market where currently only 3% of tools can detect them.
Integrate Facia with your business now and ensure an unmatched security protocol against Deepfake attacks.
Final Brief
Deepfake technology has crossed the line which it never should have. Currently, it is one of the most threatening online crimes that can cost people their entire lives or permanently damage their reputations. Many dignified people who have been victims of deepfakes attempted suicides in the worst cases. Now, the sky-rocketing number of deepfakes is circling the news daily. People need to understand the havoc that deepfake is causing and joint global efforts need to be put into place to curb the worsening situation. Deepfake detection online is no less than a challenge especially when a business or an individual is unaware of the threat and their images are manipulated without their consent. Facial recognition solutions not only ensure the protection of personal data online but also help people create fool-proof digital facial identities. Once, a business implements a solution like Facia, it is relieved from the worry of deepfake attacks in real time.
Frequently Asked Questions
Deepfake refers to an artificially created image or video recording that you might think is real but not because AI manipulated it.
Deepfake technology is a form of AI (Artificial Intelligence) that uses advanced algorithms and various deep learning techniques to synthesize media content, such as images or videos, to change the appearances or behaviors of an individual.
Deepfakes utilizes generative adversarial networks (GAN) to create realistic fakes. The process involves;
- Acquiring data; First media data is collected which serves as the foundation of the deepfake creation process.
- Generative Model Training; A deep learning algorithm is trained on the source data which allows the Generator to learn all the intricate nuances of the individual’s appearance and mannerisms.
- Deepfake Generation; Once the generator learns to create realistic fakes, the deepfake media is formed which can then be utilized for various purposes.
There are several ways to spot a deepfake:
Unnatural movements; A deepfake struggles with generating consistent facial expressions. The natural human emotion such as blinking or lip movement will appear uneven.
Skin tone and texture; The tone or texture of the face will appear to be different from the rest of the body. Moreover, if you see a blur or a sharp line around the face, it might indicate a generated image or video.
Audio Quality; Deepfakes uses software to create an artificial voice which may not be consistent with the visuals. Hence, if you hear an unnatural voice pattern that will be your cue for a deepfake.