Blog 12 Mar 2024
RELATED BLOGS

26 Jul 2024
7 minutes read
Deepfake in Movies | Facts, Fiction & Future of Film Industry
We witnessed Robert De Niro and Al Pacino defying...
View More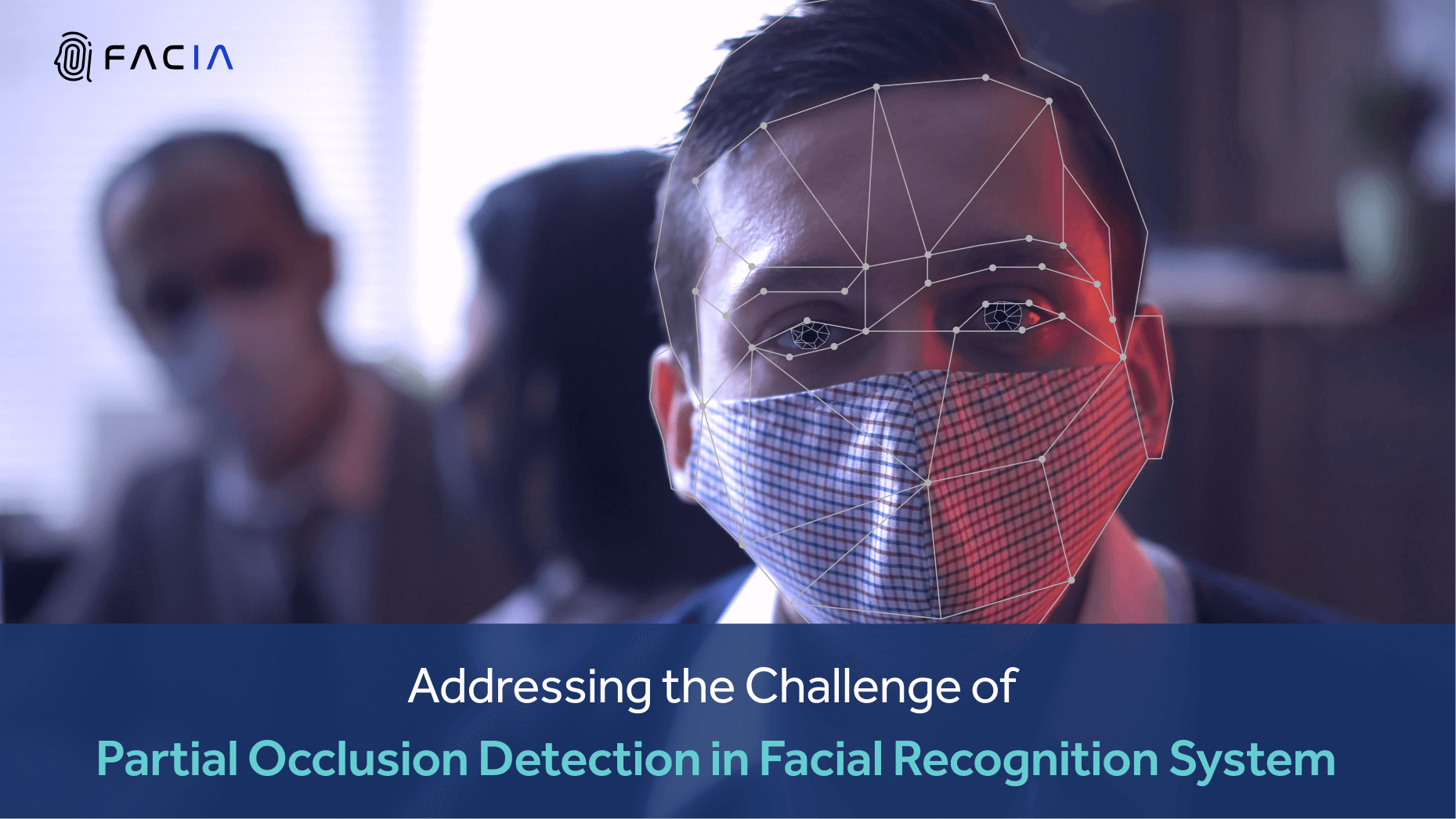
23 Jul 2024
8 minutes read
Addressing the Challenge of Partial Occlusion Detection in Facial Recognition System
People love to take pictures wearing trendy sunglasses or...
View More
20 Jul 2024
8 minutes read
Is Gait Recognition the Next Big Thing in Biometric Identity Verification?
Imagine walking towards a building where high-def cameras recognize...
View MoreSearch Blog
Search
Recent Posts



