Fight Impersonation Attacks: 7 Groundbreaking Prevention Techniques for Firms
Author: Soban K | 05 Feb 2024In This Post
Organizations face challenges in the evolving cybersecurity landscape, and a famous threat that draws everyone’s attention is an “impersonation attack”. These strikes leverage deceptive tactics and compromise user-sensitive information.
Scammers impersonate brands – a valuable asset, by using their names and putting many organizations at financial and reputational risks. Cybercriminals use text messages, mobile apps, phoney websites, voicemails, bogus emails, and social media pages in these attacks. All designed to deceive people into revealing login credentials and money transfers. Recently, a finance worker paid $25 million to a scammer, believing him to be the CFO of a multinational firm based in Hong Kong.
Key Takeaways
- Impersonation attacks involve fraudsters who pose as firm employees to gain all the company’s confidential information.
- As per the US and Canada Criminal Code, impersonation attacks are illegal.
- Companies must train employees and implement advanced AI-powered systems to restrict imposters.
- Impersonation attacks exploit human psychology. Attackers use urgency, fear tactics, or mimic trusted sources to manipulate victims into revealing sensitive information or taking detrimental actions.
What is an Impersonation Attack?
An impersonation attack is a cybercrime where attackers deceive victims by pretending to be someone they’re not, often a trusted individual, colleague, or business partner. The goal is to trick victims into revealing sensitive confidential information like login credentials, financial data, or other confidential company information.
Scammers use whaling, business email compromise, and CEO fraud to deceive high-level executives in any firm. These attacks are specifically designed to take benefit from human errors, so combatting an impersonation attack needs robust security policies.
How Do Impersonation Attacks Work?
- Social Engineering: Impersonators manipulate victims through urgency, fear, or false authority to bypass security measures.
- Email Impersonation: Emails are disguised to appear as if they come from legitimate sources, such as a company executive or a bank.
- CEO Fraud / Business Email Compromise (BEC): Attackers specifically target high-level executives to authorize fraudulent payments or wire transfers.
- Phishing: Fraudulent links or attachments in emails and messages aim to steal login credentials or install malware.
Is an Online Impersonation Attack Unlawful?
Impersonation attacks are illegal as they deceive or manipulate people to take advantage of them. According to Chapter 43, Title 18 of the US Criminal Code, the following attacks claim to be illegal:
- Impersonate any member or agent of the American Red Cross Association, 4-H youth firm, a foreign government official, or representative to commit fraud in the US, an entity that owes money to a US government employee or law enforcement officer.
- False claim to be a resident of the US.
- Search or arrest any person under the US authority figure’s guise.
Simultaneously, Section 403, Chapter C-46 of Canada’s Criminal Code declares it unlawful to impersonate someone to gain advantage or property- whether they’re dead or alive.
A Quick Glimpse of Criminal or False Impersonation
Criminal impersonation- when a scammer impersonates a victim to deceive others. The primary purpose behind this is to cause harm to the people, waste resources, and damage their reputation.
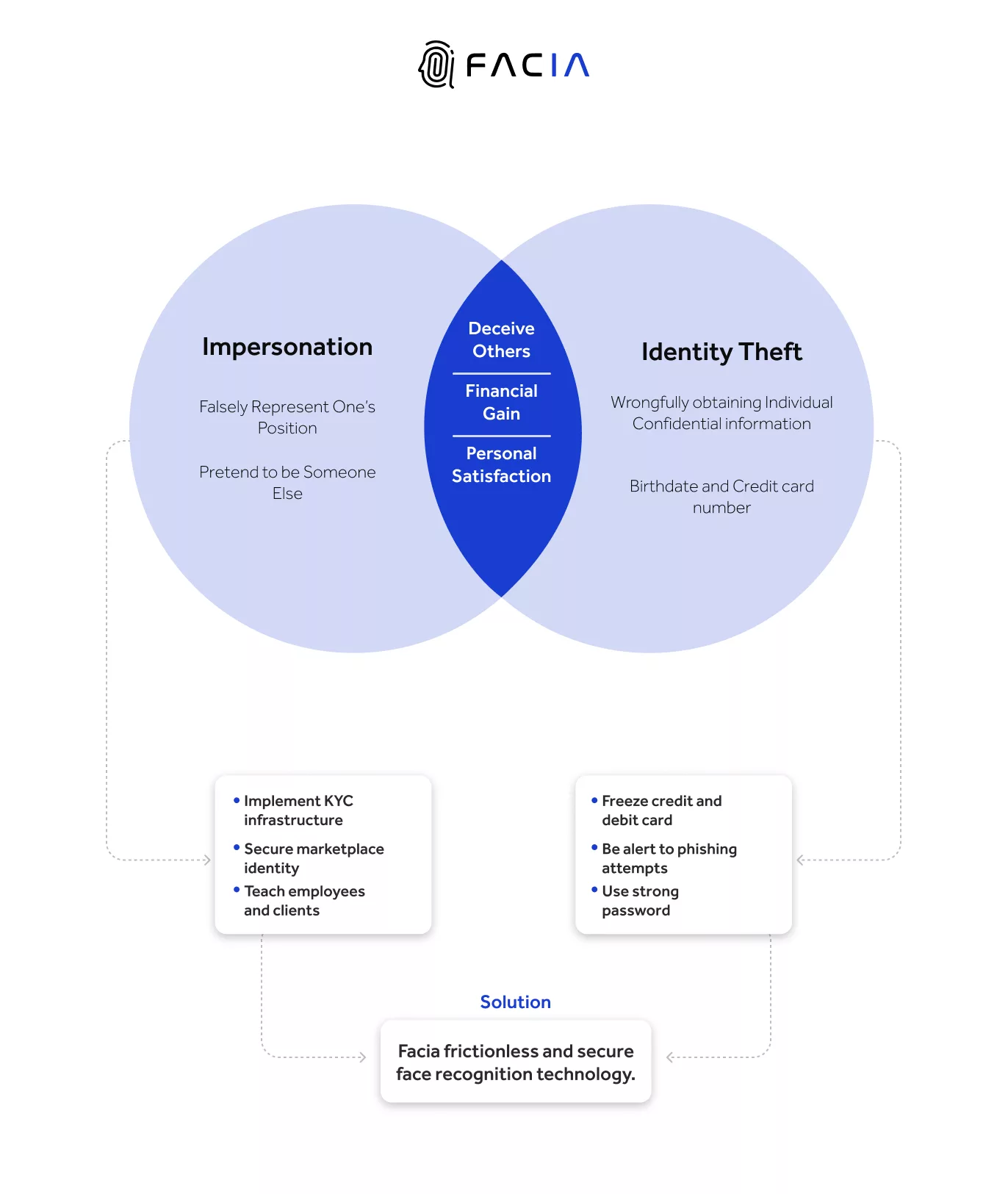
What is the Difference between Identity Theft and Impersonation?
Impersonation and identity theft are different, yet closely related. In identity theft, scammers steal someone’s identity and then use it to pretend to be them. Impersonation comes under identity theft, and their punishment is the same everywhere.
For instance, identity theft is when thieves steal someone’s purse and use their debit card. Not everyone tries to take someone’s identity for evil reasons. However, impersonators are always criminals, they just don’t steal identity, but also someone’s company and write their own name on the business license.
How Is an Impersonation Crime Executed?
Online impersonation attacks are very damaging and can be easily carried out, relying on the data type that scammers try to acquire. Attackers gather complete information about a user to gain their secured information. Sometimes, scammers target people through emails that contain links that send malware into a victim’s system.
Whaling is another method that steals the identity of the owner or manager. It involves sending direct emails to employees and requiring them to transfer money. Scammers benefit from this situation as many workers follow instructions without investigation.
How do Impersonators Plan Attacks?
Firstly, scammers gather victim information from publicly available data on the organisation’s website and social media profiles. Then, they use this data to make a realistic profile and start interacting with targeted company employees. A hacker sends any text message or email through a fake business phone number or email matching the firm’s actual number or mail. Employees are hurrying to complete their tasks, ignoring clear differences between real and fake ones.
For example,
The difference is clear between these two emails, but employees overlook this when they get hundreds of business emails per day. Hackers send emails that seem to be from authentic sources but usually contain links to fake websites that ask for sensitive information and need immediate action from the employee, such as downloading files. These files and websites are embedded with malware attacks that allow scammers to access company information easily.
Common Online Impersonation Attack Techniques
The following are some common tactics through which scammers try to impersonate victims:
Cousin Domain Attacks
A scammer creates a fake website that looks exactly like the company’s site. Rather than ending with .net or .org, their domains end with .com. Attackers send fake emails from this URL and then hack their systems when users click on a link.
Free Email Account Attack
Scammers use an email address similar to the one targeted. By using this tactic, they easily convince people to download malware and visit malicious websites, accessing their sensitive information, including credit card numbers and passwords.
Envelope Sender Attack
Rather than sending malware with a similar mail address or domain ending with .com, scammers send emails with a sender address that looks authentic, like a company. For example, [email protected]. Scammers can easily hack through this tactic, as this can bypass many filters.
Header Sender Attack
It’s an email spoofing that pushes people to believe a message was sent by someone other than its source. Scammers modify the “sender” area in an email header to incorporate an email address rather than the original one who delivered the message. They usually alter the “Return-Path” or “From” fields or sometimes both. These attacks aim to ensure that any close friend or business associate sends an email to deceive the receiver, opening the mail of someone they know.
Compromised Email Account
Fraudsters hack company employee accounts and send emails to other employees in the company. They seem like an employee with specific authority or knowledge to impersonate their colleagues.
Man-in-the-Middle (MITM) Attack
In an MITM attack, a scammer secretly intervenes and sometimes alters the discussion between two parties, who believe that they are directly talking with each other. The purpose is to impersonate one party and steal sensitive information such as login details and credentials.
CEO Fraud Attack
Fraudsters impersonate organization CEOs and convince employees to share their sensitive information by using social engineering techniques, including phone calls and phishing emails. Scammer ensures owners that they are calling from the firm’s IT department by using specific language to look real.
Strategies to Prevent Impersonation
Impersonation in the marketplace can be prevented through two procedures. Firstly, they require all related parties to provide proof of their authenticity. Secondly, they ensure all parties know how to classify marketplace communication and authentic platforms from wrong ones. The following are strategies to restrict impersonators.
Analyse and Restrict Scammers
Restricting impersonators starts with discovering and blocking scammers when they log in at any marketplace. Facial verification standards, including biometrics or liveness detection, ensure that users are legitimate. Those who don’t prove their identity must be kept out of the space.
Use Custom Email Domains
Organizations should make secure policies so both clients and employees know when they deal with real people. Firms should use domain management systems to restrict fake websites, which must be related to the social media account in conversations or link to the official website. They must analyse social networks that impersonate the employees, and it’s a marketplace. Encourage employees and clients to set strong social media account passwords and change them frequently. Companies must monitor the app stores to remove fake apps claiming to be them and use a specific email domain for effective corporate dealings.
Train Organisation Employees and Clients
Both clients and firm employees must know how to identify and handle impersonators under the following conditions:
- Avoid any URLs if they contain suspicious attachments
- Strange purchase requests, for example, gift cards in bulk
- Receive any mail from unusual locations and at a weird time of the day
- Immediately requesting any financial information or identification
- Unknown addresses and senders
Companies must remind employees and customers about their dos and dont’s over effective communication channels.
Automated and AI-Driven Software
Firms must use proactive threat intelligence and biometrics to detect different impersonation attacks and scan emails before reaching the user. Biometric systems usually cross-match email content with registered phishing attempts.
Combat Impersonation Attacks with Facia
Restricting online impersonation attacks is essential to secure firms from threats in the current dynamic cybersecurity landscape. Facia helps in mitigating these attacks by implementing strategies and advanced features including face verification and liveness detection, providing an extra security layer. Important components of a robust security system are multiple authentication factors, encryption, and continuous monitoring.
Facia incorporates AI-driven software, improving the firm’s ability to respond to and detect evolving online impersonation attacks. Train employees regarding suspicious URLs, requests, and emails, allowing for real-time identification or analysis of possible risks. By leveraging Facia, firms can significantly improve overall safety and can minimise the potential risk of becoming victims of impersonation crimes.
Want to combat impersonation attacks? Try Facia’s free trial
Frequently Asked Questions
Preventing impersonation attacks involves several key strategies: Investing in strong email security with robust spam filters and authentication protocols (like DMARC, DKIM, SPF), employee training on recognizing and handling impersonation attempts, implementing multi-factor authentication (MFA) for an added security layer, and establishing verification processes for unusual financial requests or transactions.
To detect impersonation attacks, closely scrutinize emails for misspellings, unusual addresses, and odd language, utilize technical tools like spam filters, anti-phishing software, and email authentication for suspicious activity analysis, and be wary of requests that seem out-of-character or pressurize bypassing standard procedures.
Impersonation attacks pose significant dangers, including financial loss through fraudulent payments, data theft of sensitive information or credentials, the spread of malware through malicious links or attachments, and potential reputation damage to brands and erosion of trust.
An example of impersonation is a phishing email that masquerades as being from a trusted entity, like your bank, urging you to verify your account by clicking a link and entering your login details, which leads to a counterfeit website designed to steal your information.
Impersonation attacks vary widely, including email impersonation where attackers disguise emails to appear legitimate, CEO Fraud (BEC) targeting employees by impersonating executives, website spoofing that creates fake websites to capture sensitive data, and social media impersonation involving fake profiles to deceive users into divulging personal information or clicking malicious links.