Why Passwordless Authentication is Here to Stay: A Glimpse of the Future
Author: Soban K | 09 Feb 2024In This Post
For centuries, humans have depended upon passwords to prove their identity and for security. Fernando Corbato was the first man to introduce verbal passcodes 60 years ago. In today’s world, passwords are much more complicated. A secure password must be at least 12 characters – a mixture of lower and upper case letters, special symbols, and numbers. Most social media users set identical passwords for multiple accounts, and 10% use weak passwords such as numerals or their names.
Passwords are now an outdated security method, and in a digital environment, they cannot provide enough protection for firms. Setting up strong passwords is complicated as people can’t always remember a 12-character complex sequence. Then, what’s the solution? Passwordless authentication.
The passwordless authentication market is expected to cross $40 billion by 2031 from a valuation of $12.8 billion in 2021. This growth signifies a move towards more secure, user-friendly authentication methods that align with zero trust security models and access management strategies. As authentication factors evolve, so does the need for organizations to adopt passwordless solutions that ensure strong authentication while simplifying the authentication process.
The transition from traditional password based systems to passwordless authentication reflects an understanding that security needs to be as seamless as it is robust. This shift emphasizes the importance of user authentication without compromising convenience or safety, making passwordless authentication methods a key consideration for businesses.
Key Takeaways
- Passwordless authentication removes the need for traditional, complex passwords, revolutionising the way identities are verified online.
- Passwordless authentication provides a multi-layer technique with different verification methods, including one-time codes, biometrics, and trusted devices.
- Utilizes physical items (something you have), and biometrics (something you are), and avoids vulnerable knowledge-based factors (something you know) for identity verification.
- Facia offers a passwordless authentication system, uniquely identifying users by their facial features.
What is Passwordless Authentication?
Passwordless authentication is a secure and convenient method of verifying a user’s identity without the need for a traditional password. This approach relies on alternative factors to prove who someone is, enhancing both security and the login experience.
Passwordless auth helps users with identity verification, specifically to gain access to applications, systems, and accounts without setting any complicated sequence. Multiple methods ensure accessibility, simplifying the process and strengthening digital security.
Unlike traditional methods, the Passwordless solution doesn’t save or store user data without consent or involve any complex sequence. Users can easily authenticate their identity with any type of biometrics, whether it’s facial recognition, iris scans, or palm verification.
What are the Different Approaches to Passwordless Authentication?
It’s crucial to understand the distinct approaches within passwordless authentication, often referred to as authentication factors. These factors can be categorized as something the user is (inherence), something the user has (possession), or something the user knows (knowledge).
Inherence (Something you are)
This approach leverages unique biometric characteristics for user verification.
- Fingerprint recognition: A widely used and reliable method.
- Facial scans: Increasingly common with advanced smartphone cameras.
- Voice recognition: Less secure on its own, often paired with other factors.
Possession (Something you have):
This passwordless authentication approach requires users to prove possession of a specific item for verification. This category includes:
- Physical Tokens: Dedicated security keys or smart cards grant access only when physically present. These offer a high level of security.
- Smartphones: Mobile devices are versatile, serving as a channel to receive one-time passwords (OTPs) via SMS or email, or to open authentication “magic links”.
Knowledge
While still used in some legacy systems, knowledge-based(password-based authentication) factors are generally considered less secure in modern authentication methods due to their inherent vulnerabilities.
- Security questions: These pre-defined questions require users to provide answers they have previously chosen. However, the security of this approach relies heavily on the secrecy of the chosen answers (passkey), which can be compromised through social engineering attacks or data breaches.
- PINs: Personal identification numbers, typically consisting of short numerical codes, are susceptible to brute-force attacks or simple guessing, making them a less secure passwordless authentication method.
Why Passwordless Authentication is Here to Stay
Traditional authentication methods like multi factor authentication (MFA) and single sign-on (SSO) offer security improvements, but they still rely on passwords as a base layer. This leaves vulnerabilities such as weak passwords, data exposure on unsecured machines, and the overall hassle of password management.
Due to its unlimited benefits, passwordless authentication is rapidly gaining popularity as it addresses these shortcomings, offering significant benefits:
- Enhanced Security: Passwordless authentication eliminates the risks associated with text-based passwords (phishing, data breaches, credential stuffing).
- Improved User Experience: Users enjoy a faster, frictionless login process with methods like biometric authentication or magic links.
- Simplified Management: Organizations benefit from reduced password reset requests and the streamlined administration of passwordless systems.
- Reduced Password Fatigue: Users are no longer burdened with creating and memorizing complex passwords for multiple accounts, significantly improving their experience.
- Regulatory Compliance: Passwordless authentication helps businesses comply with data protection laws like GDPR and CCPA by offering more robust user authentication.
- Flexibility and Accessibility: Diverse authentication options (biometrics, security keys, OTPs) provide adaptive authentication solutions tailored to user needs and preferences.
- Mobile-First Approach: Passwordless authentication integrates seamlessly with smartphones and tablets, aligning with the increasing use of mobile devices for accessing online accounts.
- Enterprise Scalability: These systems scale alongside growing businesses, handling large volumes of users and authentication requests without sacrificing security.
- Mitigation of Account Takeovers: Passwordless login significantly reduces the risk of account takeovers due to the inherent difficulty of replicating biometric data or compromising physical security keys.
- Future-Proof Security: By incorporating evolving technologies (like biometrics and FIDO standards), passwordless methods provide a proactive approach against emerging threats.
Most Effective Passwordless Authentication Methods
Email Magic Link
The user enters his mail during authentication, and the system quickly generates a one-time link and transfers it to the desired email address. Then, the user opens the mail and follows the link. Users must be careful and can use any verification technology to combat phishing attacks.
One-Time Password (OTP) through Text Message
OTP is the most widely used passwordless authentication technique (SMS OTP). Users just enter their phone number, receive a code through SMS, and have a limited valid period. The user quickly enters the obtained one-time code in the system and gets themselves verified.
Time-Based (OTP) or HMAC
HMAC generates an OTP password based on verification attempts that are a secret between a client and the user server. Time-based OTP is a modified form of HOTP that generates passwords according to system time. Their algorithm provides passwords on both the customer and server every time the user verifies the system. For example, Google authenticator can be used to implement this advanced algorithm.
Persistent Cookie
Persistent cookies are the widely used and simplest method to authenticate without having a password. A special cookie is installed in the user’s systems to complete authentication. This type of verification doesn’t require any data from the user.
Third-Party Identity Provider
Users can authenticate existing accounts (social login) through Facebook, Google, and Linkedin to complete the authentication process. This method is easy to use as the user is authenticated to the third-party identity provider.
Mobile Phone Biometrics
The user quickly receives notifications on his smartphone app to confirm his identity through face recognition and fingerprinting. It provides higher security as mobile phone manufacturers focus on securing from illegal accessibility. The user must set up and install the required application on his smartphone.
USB Token Device
A USB token device is a cryptographic key that authenticates the device holder quickly. It’s highly secure, as scammers can’t dodge the token.
Certificate-Based Authentication (CBA)
CBA leverages digital certificates to verify the identity of users, devices, or applications before granting access to resources. It offers a robust alternative to passwords.
How it Works
- Digital Certificates: A trusted Certificate Authority (CA) issues digital certificates. These contain a public key, identifying information, and a digital signature from the CA. A corresponding private key is securely held by the certificate owner.
- Authentication Request: When a user or device attempts to access, the server requests authentication.
- Certificate Exchange: The user/device presents its digital certificate.
- Verification: The server verifies the certificate’s validity, checks if it’s been revoked, and uses the public key to validate the CA’s digital signature.
Digital Certificates: These employ a cryptographic key pair consisting of a public key (like a freely shareable padlock) and a private key (like the only key that unlocks that padlock). Users generate this key pair when creating an account. The public key is installed on their system, while the private key is protected and often requires an authentication factor (PIN, fingerprint, etc.) for access.
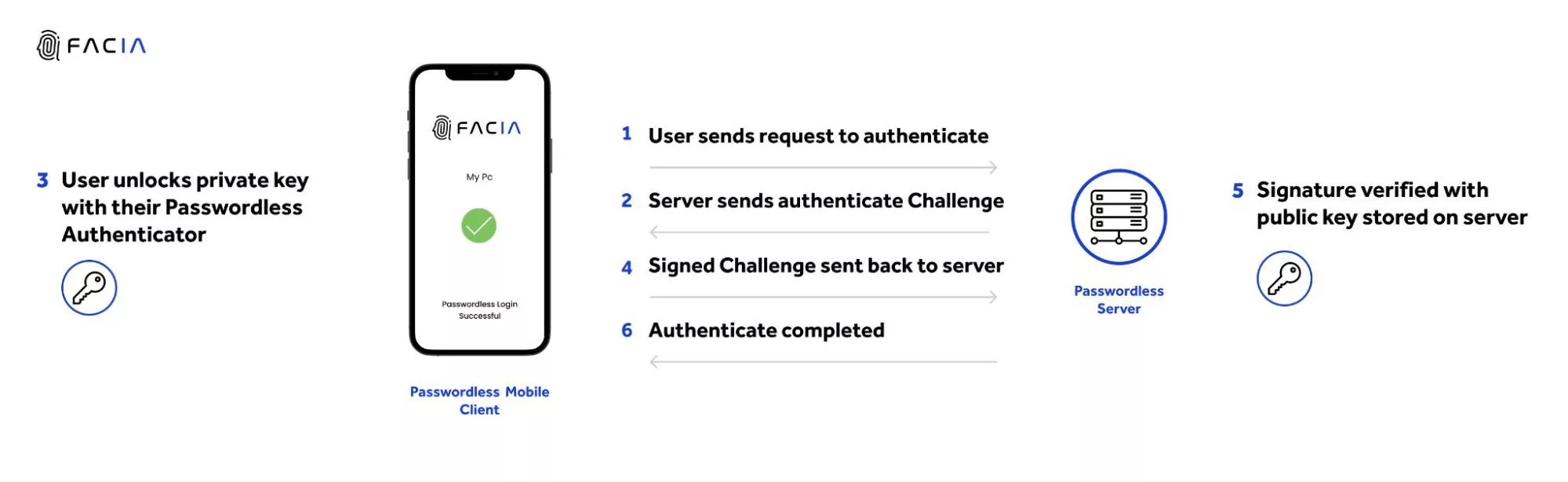
Magic Links
Magic links are famous in B2B settings as they are a secured and authenticated technique. This method is essential to email users who will enter the ID associated with a relevant account. Magic links work in the following manner:
- User accesses a web service or SaaS app
- The user is required to enter an accurate email address
- SaaS service generates a token and creates a magic link
- Magic link is sent to the email address
- The user opens the link
- SaaS thoroughly investigates the endpoint of the link
- Now, the user is all ready to start using the SaaS service
Unique Authenticators
Unique authenticators use push notifications through third-party apps, including Google authenticators. A secret code or key is issued after the admin configures the verification app with SaaS service or app through a secured channel. Then, the user will verify their identity and that all are MFA-compatible. Google Authenticator, Microsoft Authenticator, and LastPass Authenticator are some of the famous authenticator apps.
Social Log-ins
In recent years, social logins have become famous due to more usage in social media, including Apple, Google, LinkedIn, Twitter, and Facebook. Third-party service providers are identity providers, and the SaaS application redirects the user’s log-in attempts to the social media platform that authenticates the current cookie. After authentication, the access token is issued to the required user.
Improves User Security with Facia’s Passwordless Authentication Solution
Facia facial recognition technology provides a passwordless authentication system by distinctively recognizing users through facial imprints.
- The user enrolls their face within the system, which will capture a high-quality image from different angles with different lighting conditions.
- The system automatically extracts unique features from user-captured images by creating a geometrical representation referred to as a “face template”.
- This user template can be saved and compared for future authentication.
Facia’s face recognition solution is a convenient and secure alternative to conventional password based authentication.
With the Facia passwordless authentication, improve your business security!
Frequently Asked Questions
Passwordless authentication is seen as the future because it offers superior security against data breaches and phishing attacks. It eliminates the hassle of forgotten passwords and streamlines the login process for a significantly better user experience.
Two-factor authentication (2FA) adds an extra layer of security on top of passwords by requiring users to verify their identity with a second factor, like a code sent to their phone. Passwordless authentication completely replaces passwords with more secure methods such as biometrics or magic links sent to email, enhancing security and user convenience.
Passwordless authentication verifies identity using methods like biometrics (comparing physical features to a stored template), magic links (clicking a unique link sent via email), security keys (physical devices confirming identity), among other methods such as OTPs and push notifications.
Passwordless authentication generally offers enhanced safety compared to password-based systems, as replicating biometrics or compromising physical security keys is much harder than cracking passwords. However, it's crucial to use reputable providers and be aware of potential risks like phishing attempts with magic links.
Challenges with passwordless authentication include the initial investment cost, encouraging user adoption, device dependence, security concerns like data protection and phishing risks, and compatibility issues with existing systems. Addressing these challenges requires careful planning and robust security measures.