History of Identity Fraud and Identity Theft Measure
Author: Soban K | 10 Sep 2023In This Post
There was a time when identity theft was primarily a physical crime. Early perpetrators relied heavily on obtaining physical items, such as stolen wallets or mail, to impersonate others. The Social Security Number (SSN) emerged as a pivotal element in an individual’s identity.
If a cunning fraudster could acquire a combination of your name, address, or SSN, the process of impersonating you became alarmingly straightforward, leading them to unauthorized transactions and fraudulent loans.
Identity theft protection sprouted as a countermeasure to monitor these crucial identity elements. But as society transitioned into the digital era, the very definition of identity broadened. Today, an individual’s identity compasses not just their name, address, or SSN, but also digital footprints like passwords, logins, PINs, and device identifications.
History of Identity Theft
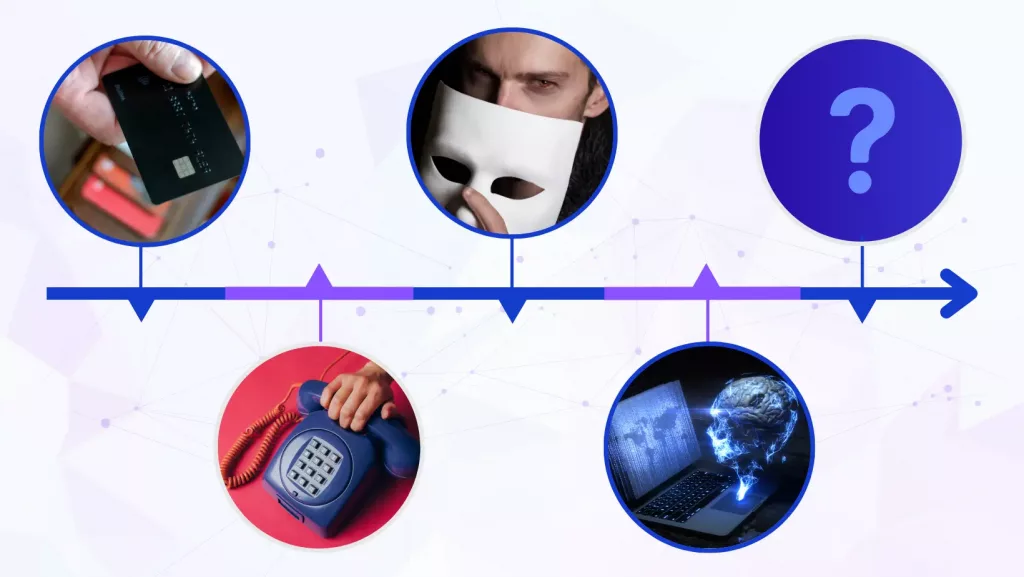
The concept of stealing someone’s identity has been around for centuries. Over time, the methods have evolved, reflecting the technological and societal shifts of each era. Let’s delve deeper into the intricate history of identity theft and how protection mechanisms have transformed.
The Birth of Identity Theft: Murder for a New Identity
Long before cybercrime became a term, stealing an identity required a dark, physical act. The victims whose identities were stolen were often murdered at the time by the first criminals. Criminals would simply take the victim’s name, his social security number, and other private information after safely disposing of the body.
The goal is to acquire a new identity, rather than money-driven. Driven by desperation or the need for a fresh start, these criminals would erase their pasts and adopt the persona of their victims.
In a time when formal identification methods were scarce, and a person’s identity depended largely on their word and signature, such drastic measures were possible.
The Telephone: Deception at a Distance
Then arrives the telephonic era; identity thieves started to commit crimes using telephones. This technological device was the first to be used in identity theft history. Promises of monetary rewards and prizes were announced to the victims using calls by these thieves.
They would then ask for private information for identity verification of the lucky winner. Victims at that time were quite willing to provide their information including social security numbers, bank account numbers, addresses, etc., as identity theft was not publicized at that time.
Instead of receiving a life-changing reward, the victim ends up with ruined credit. This was the most effective channel for almost 100% of identity fraud attempts in the 60s and 70s. Today, this channel is used by only 7% of fraudsters.
Trash-Tales: Sifting Through Secrets
The next phase popularized the use of personal paper shredders in the history of identity theft.
As telephonic identity thefts were gaining general public attention, in the meanwhile fraudsters explored another method for gathering private information. They began going through trash, looking for credit cards and bank receipts, as well as other personal identifiers.
In the 80s, victims could not have imagined that their trash might be a means to steal their identities. The public began to invest in paper shredders once this approach became acknowledged through the news.
The Digital Age: A Paradigm Shift
The dawn of the digital era marked a significant turning point in the history of identity theft, introducing new challenges and threats.
The Internet Revolution
The advent of the internet changed the game. Cybercriminals now had a vast digital playground where they could access personal information from millions of unsuspecting users.
Techniques like hacking, phishing scams, and malware attacks became prevalent. The world shrunk, and geographical barriers dissolved, enabling criminals to operate from any part of the globe, targeting victims thousands of miles away.
The technique of fraudulent activities has changed from open theft to a more refined and sophisticated illicit form, but the intent remains the same – to steal personal information for money. According to the FTC, of all identity frauds, 62% occur as a result of email fraud.
Now, fraudsters don’t have to appear in person to commit a crime. The Internet enables them to steal identities at a global level. A fraudster never has to see or speak with you to steal your identity. This is quite a change from traditional and physical theft to a technical and digital one.
Synthetic Identity Theft (Late 2000s – Present)
As technology advanced more, fraudsters started to create synthetic identities by mixing and fusing real and fake information, instead of solely using stolen data. Eventually, this made detection more challenging because these identities did not match the individual’s details completely.
Smartphones and Social Media (2010s – Present)
The rise of development in smartphones and social media channels increased the opportunities for fraudsters even more. Due to inadequate security measures of mobile apps and social networks, attackers get an easy chance to access personal information. Social media profiles are a straight gateway for data gathering.
Biometric Data and Emerging Technologies (2010s – Present)
Biometric authentication tools such as fingerprints, facial recognition, and iris scans have gained popularity now, as these are significantly secure methods to verify authentication. But, fraudsters are also devising ways to compromise biometrics of various types.
Artificial Intelligence and Deepfakes: The Future Threat
Finally, it has come down to artificial intelligence, a revolutionary technology that has changed the digital world. Creating something has never been this easy and simple. With great benefits, there are of course drawbacks, advancements in AI have allowed fraudsters to develop deepfake technology, where an individual’s video, audio, and images are analysed (impersonation technique) and used for defaming or threat purposes. Deepfakes are manipulated media created using AI algorithms.
How to Prevent Identity Fraud: Guide to Preventing Identity Fraud
Today, businesses need to stay vigilant against the ever-looming threat of identity fraud. Implementing robust protective measures is not just a choice but a necessity.
Recognizing the importance of consistent identity verification as a cornerstone for fraud prevention and cybersecurity, Facia presents a comprehensive solution tailored to your needs.
Protect Personal Information
Shred Documents: Use a cross-cut shredder for documents containing sensitive information before discarding them.
Secure Mail: Retrieve mail promptly and consider a lock for your mailbox. For outgoing mail, especially bills, drop them off at a post office box.
Limit Sharing: Only share your social security number or other personal information when absolutely necessary.
Monitor Your Finances
Regularly Check Accounts: Review bank and credit card statements regularly to ensure there are no unauthorized transactions.
Annual Credit Report: Obtain and review your free annual credit reports. Look for any unfamiliar activity or accounts.
Use Strong, Unique Passwords
Password Strength: Utilize a combination of letters (both uppercase and lowercase), numbers, and symbols.
Password Management Tools: Consider using a password manager to keep track of your passwords.
Secure Your Digital Presence
Keep Software Updated: Ensure your computer, smartphone, and other devices have the latest security patches.
Be Cautious with Emails: Avoid clicking on suspicious links. Be wary of unsolicited emails, especially those asking for personal or financial information.
Beware of Social Engineering
Stay Informed: Be aware of the latest phishing and scam techniques.
Verify Contacts: If you receive an unexpected request for personal information, double-check with the entity by contacting them directly using a verified phone number or email.
Utilize Two-Factor Authentication (2FA)
Extra Layer of Security: 2FA requires a second form of identification beyond just a password.
Protect Your Mobile Devices
Lock Your Phone: Use biometric options like fingerprint or face recognition or at least a strong passcode.
Download Wisely: Only install apps from trusted sources and be wary of apps asking for excessive permissions.
Monitor Public Exposure
Limit Social Media Sharing: Be cautious about sharing personal details that could be used to answer security questions or impersonate you.
Check Privacy Settings: Regularly review and adjust privacy settings on online accounts and social media platforms.
Respond Swiftly to Breaches
Immediate Action: If you believe you’ve been a victim of identity fraud, report it to your bank, credit card company, and the police.
Consider a Credit Freeze: This restricts access to your credit report, making it harder for identity thieves to open new accounts in your name.
Protecting yourself from identity fraud requires a combination of vigilance, education, and utilizing available security measures.
Our advanced Face verification and spoof detection system seamlessly integrates with your existing infrastructure, ensuring that identity verification is not just effective but also user-friendly. By offering a streamlined experience, we ensure customer satisfaction and trustworthiness.
Conclusion
Tracing the evolution of identity theft offers a mirror to societal and technological advancements. From brutal physical thefts to sophisticated digital deceptions, the journey underscores the adaptability of criminals.
As we continue to forge ahead in this digital age, understanding this history is not just about learning from the past but also about preparing for the future. The battle between security and deception rages on, and staying informed remains our best defence.
As we navigate this digital landscape, it’s essential to prioritize security and authenticity. With Facia, we aim to offer peace of mind through our advanced identity verification solutions. Let’s work together to create safer spaces for everyone.
Frequently Asked Questions
Identity fraud is a malicious act where someone misuses another person’s personal data, such as name and financial information, for criminal activities. This can include fraudulent credit card purchases, applying for loans in the victim’s name, or even committing crimes while impersonating the victim
Identity fraud has a long history, dating back to ancient times when people would assume false identities to evade authorities or gain illicit advantages in trade. In the modern era, The widespread use of the internet and digital communication has created new avenues for criminals to steal and misuse personal information.
Protecting your business from identity fraud is a multifaceted endeavour. Robust data security measures are essential. Employ encryption, firewalls, and secure authentication protocols to safeguard customer data. Comprehensive employee training, and proactive defenses against phishing, cyber threats, and data breaches are essential.
Identity theft can have devastating consequences for individuals. It often begins with unauthorized financial transactions. These losses can be challenging to recover, involving disputes with financial institutions. In addition to financial distress, identity theft can damage an individual’s credit history, making it difficult to secure loans or credit cards in the future.
The four notable identity theft cases in recent years include David Matthew Read’s sophisticated fraud, Turhan Armstrong’s complex schemes, Kenneth Gibson’s exploitation of data breaches, and Luis Flores’s use of synthetic identities for illicit financial activities. These cases emphasize the enduring threat of identity theft in the digital age.