1:1 Matching and 1:N Matching: Two Mechanisms for Enhanced Facial Identity Proofing
Author: admin | 03 Jun 2024In This Post
Have you ever wondered if there’s a difference between having your face scanned at the airport and scanning it to unlock your phone? The answer is yes, there is, and just how big of a difference might surprise you.
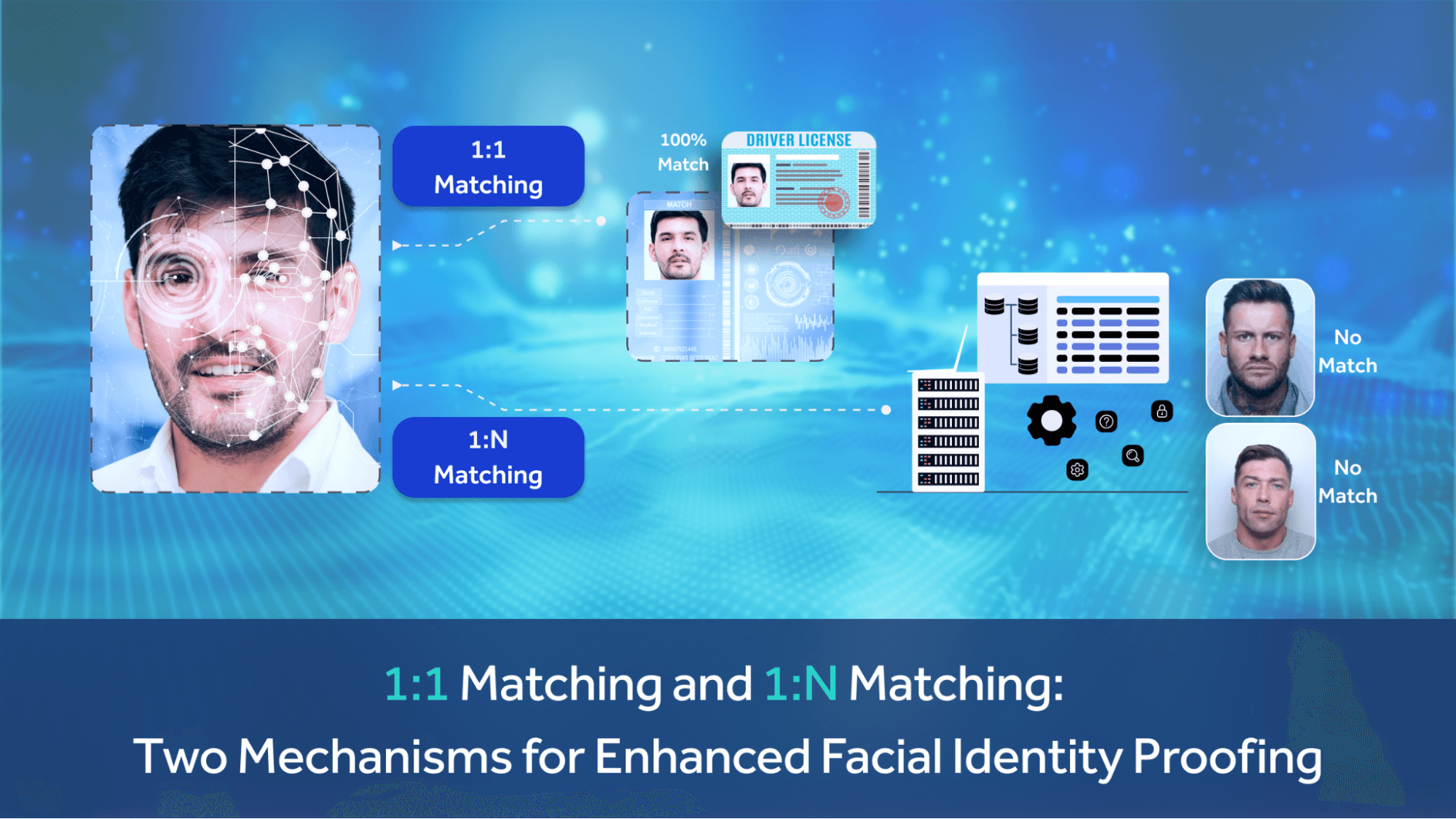
The distinction lies in the two major kinds of matching processes involved in modern biometric security: 1:1 matching and 1:N matching. The two of these form the major pillars of how we as individuals in today’s day and age are identified, without having to remember complex passwords.
But what is the difference between these two? How are these processes carried out? And when is one used and the other isn’t? Learn the answer to these questions and a lot more in today’s detailed blog.
Modern Security and Authentication with Biometrics
Advancements in one domain of technology have the side effect of creating improvements in other domains. As artificial intelligence technologies like neural networks and deep learning advanced, face recognition and biometric verification benefited as a result.
In today’s world, it is no longer required that the average person remember long and increasingly complex passwords or PIN codes to access secure systems. At the same time, organizations do not have to rely on physical documentation and all the possibilities of forgery, fraud, and other illicit activities that come with them to identify an individual.
The different biometric traits that are intrinsically linked with every individual, things like your face, fingerprint, and so on, work as some of the most secure access keys that every person has.
Now, depending on the situation, these biometric traits and markers can be utilized in one of two ways:
1:1 Matching: Authenticating People
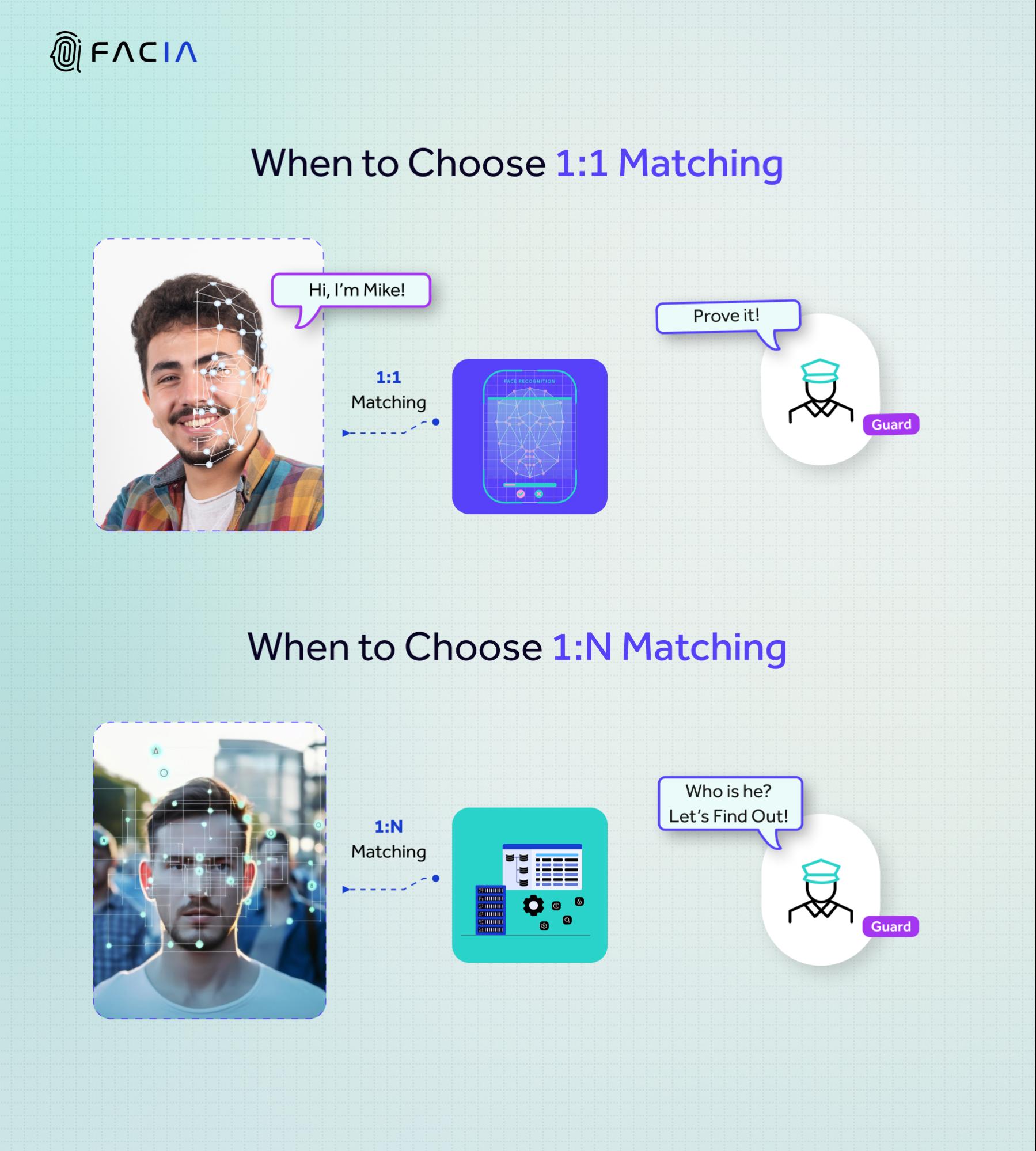
The first, and slightly more simple of the two processes is 1:1 matching. As indicated by the name, this procedure involves analyzing an input face to see if it matches one of a set of previously saved faces.
Mechanism
In this scenario, the goal is to verify that the person is one of a set of people already allowed access to a system, space, or building. This is why the technical mechanism is referred to as a ‘1 to 1 match’.
The set of approved faces is generally stored locally/on-premises, and so the system usually does not require to be connected to the internet or some cloud server to work. This also means that the process works much faster, and is relatively much less resource and computationally intensive to carry out.
Use Cases
- Device Authentication: The most common and simple use case of this form of biometric security is to secure your private devices, including your phone, tablets, laptops, and so on. In this case, the system simply checks if the input face matches what is usually a single stored template.
- Access Control: Controlling access to restricted or private areas, rooms, or buildings is carried out through the mechanism of one-to-one matching, like a company premises, or an employee-only area in a public establishment. This kind of system ensures that only approved individuals are allowed into designated spaces without the need to match IDs with faces manually.
- Approving Actions: Identity matching is often used as an additional measure of security at the time of a financial transaction, to make sure that the transaction is being carried out by, or with the approval of, the account holder.
Read More: Photo ID Matching with Real Time Identity Verification
1:N Matching: Identifying People
The other of the two fundamental processes involved in the use of biometrics for security is 1:N matching. This procedure involves running an input face through a database, or multiple databases, to see if there is a record available with the same face.
Mechanism
In contrast to one-to-one, in this scenario, the identity of the individual is not known, and the goal is in fact to find out or identify who the person is. The face would be compared against an indeterminate number of records until some match is found. This is why the technical mechanism for this process is referred to as the ‘1 to N match’ (or ‘one to many’ match).
Since the database that the face is being compared against is usually some form of national or otherwise large-scale record, it is located in some form of remote or cloud storage. This combined with the comparatively massive number of matching operations carried out for a single individual means that this process takes longer, and is much more resource-intensive.
Use Cases
- Law Enforcement: One of the most beneficial uses of an identity match is to discern the identity of suspects in a criminal case through the use of surveillance footage or other publicly available images or videos.
- Individual Screening: Watchlist matching a face is something done quite commonly by many companies before hiring an employee. Many financial institutions also go through a process of watchlist screening before engaging in any form of partnership or professional relationship with an individual.
- Checkpoint Security: A 1:N matching system at airports, borders, and other security checkpoints allows for faster processing of individuals and quicker identification of potential threats.
| – | 1:1 | 1:N |
| Purpose | To Authenticate the individual. | To Identify the Individual. |
| Scope | Smaller Scale, a single company for example. | Large-scale, usually national or international databases. |
| Action | Verifying someone’s Identity | Searching for someone’s identity |
| Database | Local | Remote |
Read More: Face Matching Technology Future of Secure Authentication
Spoofing Attacks: A Tricky Situation
Even with how relatively new biometric security systems are, there are already malicious individuals who make attempts to trick and gain unauthorized access to them. The main tool that is used by these individuals to attempt to fool the system into giving them access is known as a spoof.
A spoofing attack is when a malicious individual pretends to be another person by utilizing a fake, digital recreation of that person. In the field of facial biometrics, this takes the form of a presentation attack. Where the attacker ‘presents’ a synthetic recreation of an approved person’s face to the camera.
The attack tool usually is either a high-quality photo, video, deepfake, or 3D mask of the approved person. The goal is for the system to think that the actual person is in front of the camera, and provide access.
The Ideal Solution – Liveness Detection
By far the best way to prevent potential spoofing attacks during biometric matching processes is to use a liveness detection solution. Liveness detection works to identify whether the input provided to the facial recognition system is from a live individual present in the room themselves, or some digital or synthetic fake.
The way it does that is by working on one of two kinds of mechanisms: active and passive. In passive liveness detection, the system analyzes the input provided to the camera to see if there is natural micro-movement indicative of a real human being.
The other method is active liveness detection. In this process, the system prompts some facial movement from the user, like turning their head or smiling at the camera. It then analyzes this movement to detect natural human movement.
In this way, liveness detection helps to present spoofing attacks and eliminate the possibility of malicious activity in biometric security systems.
In a world where individuals want faster and faster access to their devices and systems, 1 to 1 matching can provide the perfect authentication solution over conventional pins and passwords. Better awareness of these systems’ security can lead to more widespread adoption of facial unlocking. Similarly, with 1 to N matching, the speed with which regular security procedures in multiple industries are conducted is and can be enhanced exponentially with the more widespread integration of facial recognition solutions. To learn how you can integrate this tech into your existing system, contact Facia today.
Frequently Asked Questions
In 1:1 matching, the system tries to verify if the individual trying to gain entry is one of a set of pre-approved individuals. So, the identity is known, the system is just trying to confirm the identity.
In 1:N matching, the system is trying to discern the identity of the individual by running their face through some database. So, the goal is to figure out who the individual is in the first place.
1:1 matching ensures accuracy through its key mechanism of exactly matching every single characteristic in the input face against the same characteristic in the comparison face. This direct comparison ensures that each pair of faces matches each other exactly. The specificity of this mechanism also reduces the possibility of false matches or rejections.
1:1 matching is a much quicker and frictionless method of verifying a person’s identity than manual verification methods like checking IDs and other documents and comparing. It is also faster than pin codes, passwords and other methods of verifying and providing access to systems. It also reduces the possibility of unauthorized access by utilizing biometric markers for access that are unique to the individual.